There are many adjectives that could be used to describe the global outbreak of COVID-19, but perhaps the simplest might be: fast.
The disease has...
As IoT adoption continues to proliferate, manufactures and adopters are increasingly aware of cybersecurity risks to IoT. Yet, even among the IoT security professionals,...
In one of those strange inversions of reason, The Internet of Things (IoT) arguably began before the Internet itself. In 1980, a thirsty graduate...
In their outstanding book, Wicked and Wise, Alan Watkins and Ken Wilber look at some of the most pressing ‘wicked problems’ facing the human...
Canada has been investing in machine learning and artificial intelligence (AI) for longer than most of the industrialized world. Dr. Geoff Hinton of Google...
Ultra high speed, high quality 5G networks are expected to provide the connectivity required for massive IoT adoption, remote robotic surgery as well as...
Getting smart about security in smart systems
Smart used to be something we called people or pets. It wasn't a term one would use to...
The telecoms and digital technologies sectors are notoriously jargonised. Eavesdrop on any conversation at an industry conference (remember those?) and you’d be treated to...
Bluetooth is short-range wireless communications technology based on the IEEE 802.15.1 protocol. It works in a crowded license free 2.4 GHz frequency band and...
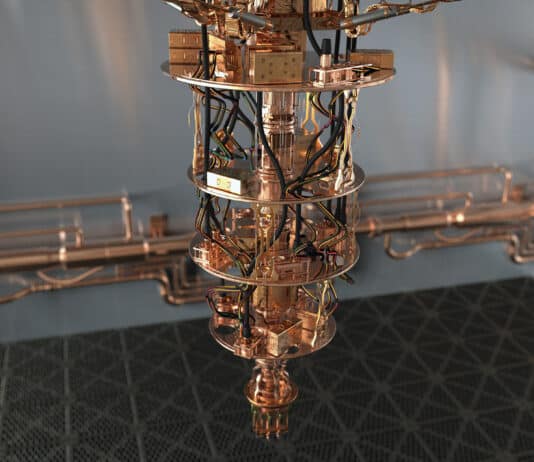
The secret sauce of quantum computing, which even Einstein called "spooky," is the ability to generate and manipulate quantum bits of data or qubits. Certain computational tasks can be executed exponentially faster on a quantum processor using qubits, than on a classical computer with 1s and 0s. A qubit can attain a third state of superimposition of 1s and 0s simultaneously, encode data into quantum mechanical properties by "entangling" pairs of qubits, manipulate that data and perform huge complex calculations very quickly.
IoT Wireless Protocols data rate and range comparison in a spreadsheet format. Includes downloadable Excel spreadsheet.
In a major milestone for 5G, 3GPP finalized the Release 16 in July - its second set of specifications for 5G New Radio (NR)...
Don’t let the “5G” in the title confuse you. This post is not only about the telcos’ core networks, but about the 5G security...
Depending on who you speak to, 5G is either humankind’s greatest imminent blessing or its greatest imminent curse. Still in its infancy, and not...
No, no it doesn’t. Huawei's code might as well be extremely secure. Their code is certainly the most scrutinized. But the recent UDG source...