It's been a year of contradictions for the telecommunications industry.
Like most sectors, it has been heavily impacted by the consequences of the Covid-19 pandemic,...
In the recent report by IHS Markit - "The 5G Economy - How 5G will contribute to the global economy" - researchers claimed that...
Neil Harbisson calls himself a cyborg. Without the antenna implanted in his skull, he would not be able to see colour of any kind....
The interest in 5G and mIoT is exploding. It's exciting to see so many IT and cybersecurity professionals in my network trying to learn...
In a major milestone for 5G, 3GPP finalized the Release 16 in July - its second set of specifications for 5G New Radio (NR)...
No, no it doesn’t. Huawei's code might as well be extremely secure. Their code is certainly the most scrutinized. But the recent UDG source...
IoT Wireless Protocols data rate and range comparison in a spreadsheet format. Includes downloadable Excel spreadsheet.
IoT Wireless Protocols in a spreadsheet format. Includes downloadable Excel spreadsheet.
For many end-users of today's communications technology, the cloud is a somewhat mystical concept, a digital equivalent of aether. Most think of it as...
There are many adjectives that could be used to describe the global outbreak of COVID-19, but perhaps the simplest might be: fast.
The disease has...
Depending on who you speak to, 5G is either humankind’s greatest imminent blessing or its greatest imminent curse. Still in its infancy, and not...
In their outstanding book, Wicked and Wise, Alan Watkins and Ken Wilber look at some of the most pressing ‘wicked problems’ facing the human...
The human will to innovate is seemingly relentless. The history of our species is one of continual development, with the last 350 years, in...
In 1967, Lynn Margulis, a young biologist, published a paper that challenged more than a hundred years of evolutionary theory. It proposed that millions...
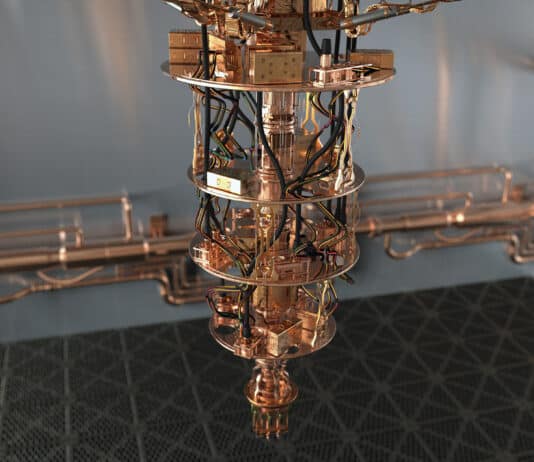
The secret sauce of quantum computing, which even Einstein called "spooky," is the ability to generate and manipulate quantum bits of data or qubits. Certain computational tasks can be executed exponentially faster on a quantum processor using qubits, than on a classical computer with 1s and 0s. A qubit can attain a third state of superimposition of 1s and 0s simultaneously, encode data into quantum mechanical properties by "entangling" pairs of qubits, manipulate that data and perform huge complex calculations very quickly.