Tag: OPINION
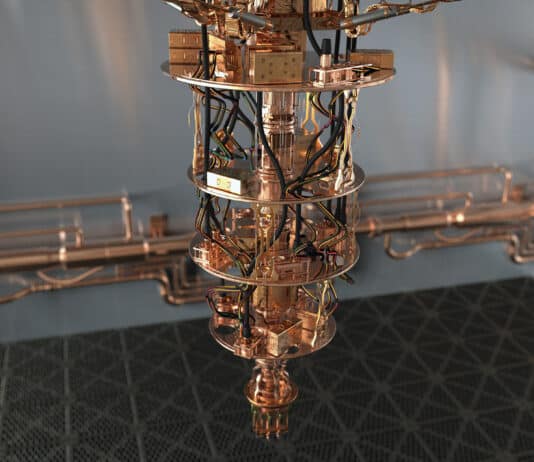
The secret sauce of quantum computing, which even Einstein called "spooky," is the ability to generate and manipulate quantum bits of data or qubits. Certain computational tasks can be executed exponentially faster on a quantum processor using qubits, than on a classical computer with 1s and 0s. A qubit can attain a third state of superimposition of 1s and 0s simultaneously, encode data into quantum mechanical properties by "entangling" pairs of qubits, manipulate that data and perform huge complex calculations very quickly.
When microwave ovens first arrived on the market in 1967 they were met with public skepticism. Perhaps it was because, not long before, the...
The timeline of human history is marked by inflection points of major technological advancement. The plow, the printing press, the telegraph, the steam engine,...
In my previous post I argued that if Canada wants to succeed with its AI-focused innovation agenda, it should also be at the forefront...
The rollout of 5G is one of the most anticipated events in humanity’s technological history. But what about the 5G health concerns?
It’s the night...
Canada has been investing in machine learning and artificial intelligence (AI) for longer than most of the industrialized world. Dr. Geoff Hinton of Google...
If you've ever been to an expensive restaurant and ordered a familiar dish like, say, lasagna, but received a plate with five different elements...
Because it demands so much manpower, cybersecurity has already benefited from AI and automation to improve threat prevention, detection and response. Preventing spam and identifying malware are already common examples. However, AI is also being used – and will be used more and more – by cybercriminals to circumvent cyberdefenses and bypass security algorithms. AI-driven cyberattacks have the potential to be faster, wider spread and less costly to implement. They can be scaled up in ways that have not been possible in even the most well-coordinated hacking campaigns. These attacks evolve in real time, achieving high impact rates.
In 2013, George F. Young and colleagues completed a fascinating study into the science behind starling murmurations. These breathtaking displays of thousands – sometimes...
Not even 30 years separate us from the end of the Cold War. Yet, we appear to be witnessing the emergence of a new...
5G connectivity burst onto the world stage at last year’s Winter Olympics in Seoul, South Korea and gained pop culture visibility again at the...
Quantum computing holds the potential to revolutionize fields where classical computers struggle, particularly in areas involving complex quantum systems, large-scale optimization, and cryptography. The power of quantum computing lies in its ability to leverage the principles of quantum mechanics—superposition and entanglement—to perform certain types of calculations much more efficiently than classical computers.
Emerging Technology and Geopolitics of 5G
There are several reasons emerging technology is a highly competitive industry, notwithstanding the race for intellectual property that can...
Ultra high speed, high quality 5G networks are expected to provide the connectivity required for massive IoT adoption, remote robotic surgery as well as...
Don’t let the “5G” in the title confuse you. This post is not only about the telcos’ core networks, but about the 5G security...