Tag: ARTICLE
In their outstanding book, Wicked and Wise, Alan Watkins and Ken Wilber look at some of the most pressing ‘wicked problems’ facing the human...
The human will to innovate is seemingly relentless. The history of our species is one of continual development, with the last 350 years, in...
In 1967, Lynn Margulis, a young biologist, published a paper that challenged more than a hundred years of evolutionary theory. It proposed that millions...
Model stealing, also known as model extraction, is the practice of reverse engineering a machine learning model owned by a third party without explicit authorization. Attackers don't need direct access to the model's parameters or training data to accomplish this. Instead, they often interact with the model via its API or any public interface, making queries (i.e., sending input data) and receiving predictions (i.e., output data). By systematically making numerous queries and meticulously studying the outputs, attackers can build a new model that closely approximates the target model's behavior.
The full story behind the first major crypto hack and how much really was lost.
MtGox was one of the very first platforms on which...
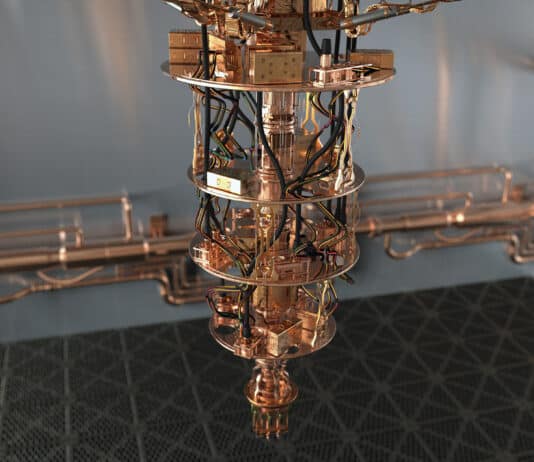
The secret sauce of quantum computing, which even Einstein called "spooky," is the ability to generate and manipulate quantum bits of data or qubits. Certain computational tasks can be executed exponentially faster on a quantum processor using qubits, than on a classical computer with 1s and 0s. A qubit can attain a third state of superimposition of 1s and 0s simultaneously, encode data into quantum mechanical properties by "entangling" pairs of qubits, manipulate that data and perform huge complex calculations very quickly.
When microwave ovens first arrived on the market in 1967 they were met with public skepticism. Perhaps it was because, not long before, the...
The timeline of human history is marked by inflection points of major technological advancement. The plow, the printing press, the telegraph, the steam engine,...
In my previous post I argued that if Canada wants to succeed with its AI-focused innovation agenda, it should also be at the forefront...
The rollout of 5G is one of the most anticipated events in humanity’s technological history. But what about the 5G health concerns?
It’s the night...
Canada has been investing in machine learning and artificial intelligence (AI) for longer than most of the industrialized world. Dr. Geoff Hinton of Google...
NFC is a short range two-way wireless communication technology that enables simple and secure communication between electronic devices embedded with NFC microchip. NFC technology...
Radio-Frequency Identification (RFID) is a technology commonly used for identification, status administration and management of different objects. It is important for people identification, as it...
If you've ever been to an expensive restaurant and ordered a familiar dish like, say, lasagna, but received a plate with five different elements...
The Wi-Fi represents wireless technology that includes the IEEE 802.11 family of standards (IEEE 802.11a, IEEE 802.11b, IEEE 802.11g, IEEE 802.11n, IEEE 802.11ac, etc.)....