The Wi-Fi represents wireless technology that includes the IEEE 802.11 family of standards (IEEE 802.11a, IEEE 802.11b, IEEE 802.11g, IEEE 802.11n, IEEE 802.11ac, etc.)....
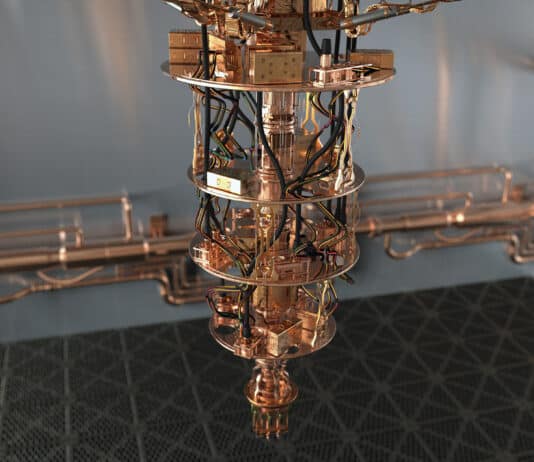
The secret sauce of quantum computing, which even Einstein called "spooky," is the ability to generate and manipulate quantum bits of data or qubits. Certain computational tasks can be executed exponentially faster on a quantum processor using qubits, than on a classical computer with 1s and 0s. A qubit can attain a third state of superimposition of 1s and 0s simultaneously, encode data into quantum mechanical properties by "entangling" pairs of qubits, manipulate that data and perform huge complex calculations very quickly.
Radio-Frequency Identification (RFID) is a technology commonly used for identification, status administration and management of different objects. It is important for people identification, as it...
The attacker stepped out from behind a hedge in the upper-class suburban neighborhood, being careful to stay in the shadows. Across the street, the...
Cybersecuring railway systems from potential attackers must become paramount in the digitization that those systems currently undergo. Their cybersecurity is too closely interlinked with...
In their growing efforts to increase efficiencies through digitization and automation, railways are becoming increasingly vulnerable to cyber-kinetic attacks as they move away from...
Getting smart about security in smart systems
Smart used to be something we called people or pets. It wasn't a term one would use to...
The maritime industry faces a not-so-distant future when ships will be completely autonomous, using navigation data that they receive to plot their own courses...
In one of those strange inversions of reason, The Internet of Things (IoT) arguably began before the Internet itself. In 1980, a thirsty graduate...
Western publications often picture the People’s Democratic Republic of China (hereafter China) as the world’s chief propagator of cyberattacks. But the picture is much...
The human brain is programmed to keep us safe and secure. Yes, we are separated from the rest of the animal kingdom by our...
Stuxnet was the first true cyber-kinetic weapon, designed to cripple the Iranian – and perhaps also the North Korean – nuclear weapon programs. It...
More than half of the world’s population lives in cities. The UN estimates that by 2050 that proportion will be 68% - more than...
The open seas have long attracted those who yearned for adventure. The risk of pitting oneself against a vast and unforgiving sea has tested...
The attacker stepped out from behind a hedge in the upper-class suburban neighborhood, being careful to stay in the shadows. Across the street, the...